Is your organization facing these problems?
Internet-connected devices within organization became Botnet that has been used to perform DoS/DDos attacks
If either one is true, SRAN can help you solve these problems with our ready-to-use appliance with Log Management feature plus Network Security Monitoring. Be Save, Be Secure!
Excessive Bandwidth usage which could cause unstable internet connection
If either one is true, SRAN can help you solve these problems with our ready-to-use appliance with Log Management feature plus Network Security Monitoring. Be Save, Be Secure!

No Log Management implementation to comply with Computer-Related Crime Act B.E.2560
If either one is true, SRAN can help you solve these problems with our ready-to-use appliance with Log Management feature plus Network Security Monitoring. Be Save, Be Secure!
Automatic Identification Device
- Know Device / Unknown device
- Approve Device / Rogue Detection
- BYOD : Desktop / Mobile
- Inventory : Device
Detection
- Attack Detection (Brute force, exploit)
- Malware/Virus Detection
- Detection Software
- Bittorent Detection
- Tor/Proxy Detection
Log Analysis
Security Information Event Management
- Threat Analysis
- Risk Analyzer
Bandwidth Monitoring
- Protocol and Bandwidth Usage
- Application Monitoring (Software Bandwidth Usage)
- Social Network Monitoring (Facebook, Line, Youtube, Pantip)
- User Monitoring
Deep Search
- Network Forensic Evident Data
- Conditional Search
Log Archive / Log Audit
- Raw Full Data
- Support AD (Active Directory)
- Export Data
- Integrity Hashing
- Active Directory Login Success/Login Fail, SSH Login Success/Login Fail
Protection
- Web Filtering (Advertisements Block, Anti-Phishing, Antivirus/Malware)
Report
- Executive Summary
- Compliance Thai Cyber Law Log Correlation Report
- HTTP/SSL Analyzer
SRAN Cyber Security
Full Functional Network Security and Logging Report
Comprehensive network traffic analysis and security monitoring
Analyze and monitor network traffic
Identify bandwidth-hogging users and applications
Threat analysis
Protocol analysis and record
Report
4 reasons to have SRAN secure your network
Our Experience and Expertise
With Our Experience and Expertise for more than 20 years in research and development of cybersecurity products, you can rely on our product quality and efficient services.
All-in-One Product
All-in-One Product SRAN features include Log Management and Network Security Monitoring, so your network will be strongly secured with regulatory compliance.
User-Friendly Appliance
User-Friendly Appliance Easy to install, no more IT expert needed. Many models are available according to numbers of users and sizes of each organization.

Worth Your Investment
Worth Your Investment Paying less money and getting more benefits while Thai people can control own cybersecurity technology for the sake of Thailand.
Why Companies Increase Investment in Cyber Security
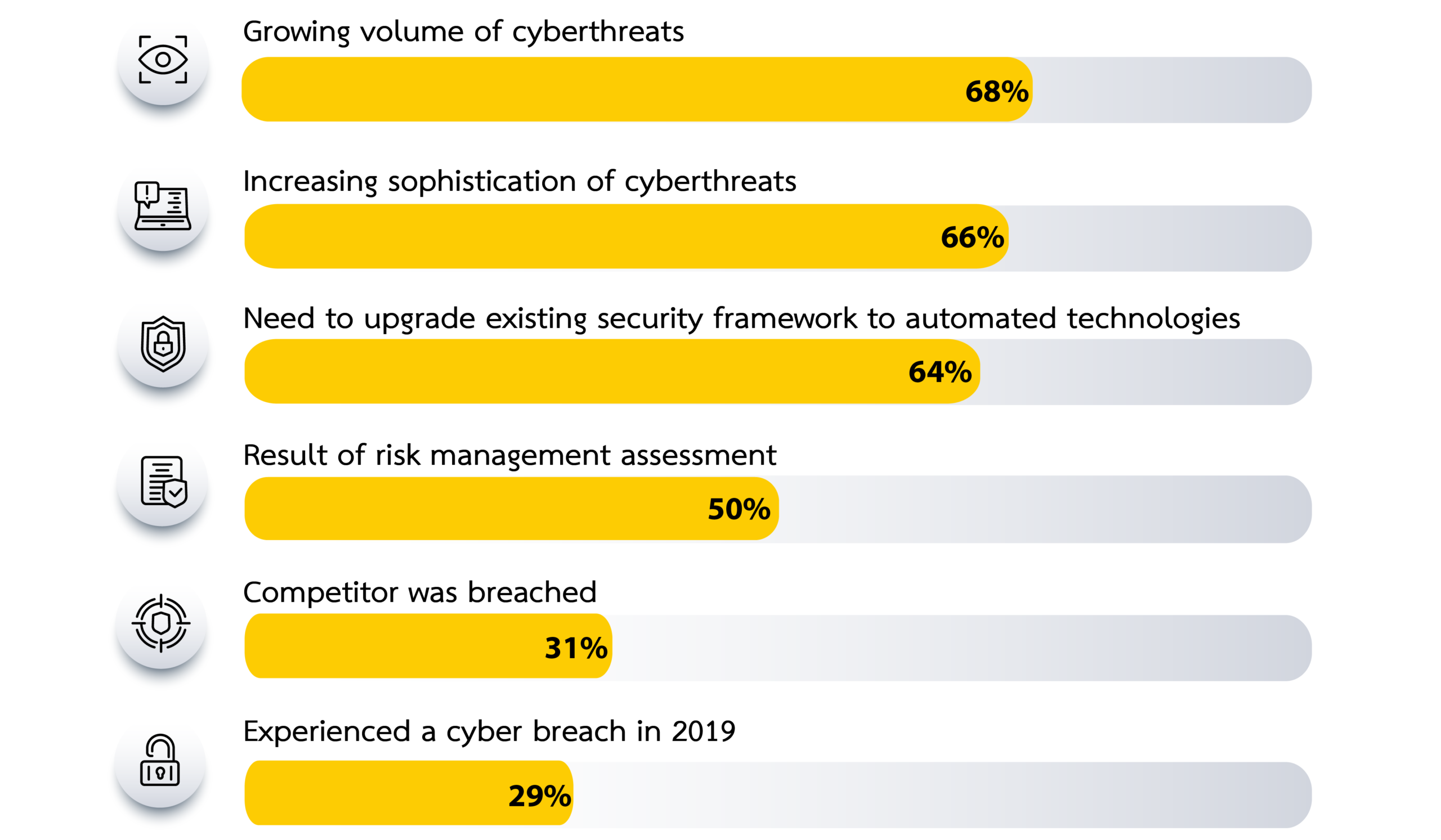
Source: Palo Alto Networks, The State of Cybersecurity in ASEAN, 2020
Top 6 Cybersecurity Threats in Thailand in 2020
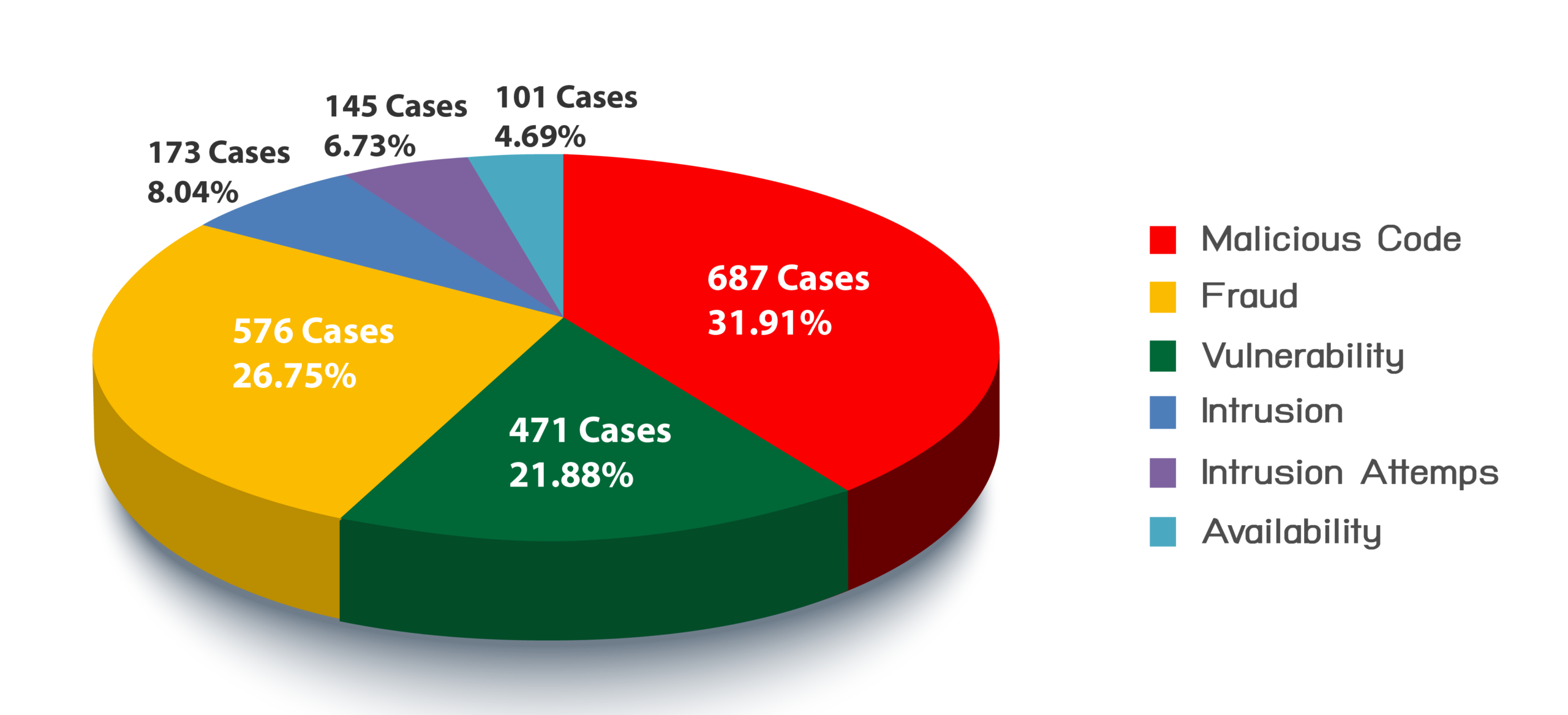
Source: Thaicert
News and Events
-
Team Building Activities in Osaka, Japan during 27 Feb – 2 Mar 2019
Global Technology Co., Ltd. has organized a team building activity in the city of Saoca, Japan, between 27 February -
-
New Year’s Eve party on December 27, 2018
SRAN held a New Year's Eve party to welcome the new year on December 27, 2018, led by Mr. Narat
-
SRAN Booth at Thailand Software Expo 2018
Thai Software Industry Association (ATSI) would like to invite you to attend the software show and listen to the seminar



























































































































































































































































































































































































































